The background of this layout should be an image. Please use Change Background feature to change the background of this layout.
(Can be found under DESIGN tab)
COLORID - IDENTITY MANAGEMENT
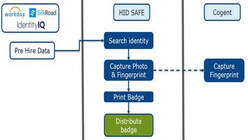
The concept of identity management currently covers the systems and hardware that converge on the production of an ID card. Each system and directory operates independently, sharing data on demand with applications via file transfers or direct database connections. The ID card production database is usually authoritative for card-related identity elements and would often be described as the heart of a university’s identity management system.
This loosely connected approach has worked well enough with legacy on-premises systems. Proprietary databases, overprotective system admins and buggy applications could often be circumvented by manual operations, if necessary. For example, if a school had an access control system that was managed by a separate department, which did not allow read or write access to the database, the card office would capture the preprogrammed prox card numbers and send them to that system admin, who would enter them by hand.
As more independent systems, databases and third-party applications (many of them hosted in the cloud) are connected, the traditional approach is being stretched to the breaking point. Legacy systems may not support modern database connections, or they may require expensive and time consuming professional services to create connections that may break with each windows or application update.
This loosely connected approach has worked well enough with legacy on-premises systems. Proprietary databases, overprotective system admins and buggy applications could often be circumvented by manual operations, if necessary. For example, if a school had an access control system that was managed by a separate department, which did not allow read or write access to the database, the card office would capture the preprogrammed prox card numbers and send them to that system admin, who would enter them by hand.
As more independent systems, databases and third-party applications (many of them hosted in the cloud) are connected, the traditional approach is being stretched to the breaking point. Legacy systems may not support modern database connections, or they may require expensive and time consuming professional services to create connections that may break with each windows or application update.
ABSTRACTEstablishing and keeping track of all the identities of personnel is more important than ever, both for security and enhanced user experience. Today each system manages user identities as required for its own purposes, occasionally sharing data with other systems operating similarly. New products are available which provide identity management across all organization systems with administrative access from any PC or mobile device, reporting and analytics, and support for future identity technologies regardless of existing platforms.
|
WEB-BASEDNetwork-focused application design has begun to appear in the newest identity-related products. Such an application and its web service software, resident on a PC or dedicated server, is accessed through a web browser on the same or any other machine on the network, via a web browser. If the application is hosted offsite, such as in Amazon Web Services or Microsoft Azure, it would be called cloud-based. Locally hosted, web-based applications can be purchased outright, while cloud-based services are usually sold on a subscription basis.
|
These application models present new challenges in supporting ID card production and data transfers. Cameras and ID printers may be supported by Windows drivers at each local machine, but more sophisticated functions could require additional drivers on each PC. File transfers between cloud servers and the university’s LAN often require development involving APIs and SSL- or SFTP-protected data communications.
DATA & LIMITATIONSWith identity data and controlling policies distributed across so many networks and locations, efficient management is difficult. Pulling reports and implementing organization-wide policies can become multi-layered processes, if they are possible at all. Major one-card systems offer some of these services, but high fees for system connections, custom development and report building, in addition to slow response times, have become good reasons for not exploring options outside of the system providers menu.
|
This has worked well for the one-card system providers, but not so well for universities that want to pursue tech solutions that are created with an eye to a new generation of identity management solutions.
NEW PRODUCTSNew software products and services are available which provide comprehensive identity management, from identity vetting and document capture to database provisioning according to centrally managed rules and policies. These new solutions are designed to connect to any new or existing systems by the most efficient methods available, whether API’s, file transfers or direct database connections. Self-service web portals for registering and deactivating credentials, web-based administrative GUIs (Graphical User Interface), user-friendly report builders and robust analytics are some available features. If data aggregation and visualization across databases are needed, services are available for those functions also.
|
A true identity management system becomes the new authoritative source from which documented, vetted and centrally managed identity data flows to all applications that process identity data, including ID card issuance, the one-card system for financial transactions and physical access control systems.
THE FUTUREIdentity management systems provide a platform for supporting new technologies, independent of major one-card system offerings. By analyzing data from all the connected databases, system intelligence will be able to predict events and automatically grant or deny access to doors, payment systems or networks. Geolocation will also be used to make these decisions. An identity management system can also provide support for sophisticated contactless card encoding, mobile credential platforms, visitor manager applications and other third-party systems, whether cloud-based or on-premises.
|
PRODUCTS & RESOURCES
REQUEST MORE INFORMATION
WE'RE HERE TO HELP.
|
ColorID has spent over 24 years serving the ID Industry with top-level sales and support to build the ultimate trust with every customer.
|
|
|
|
ColorID's interactive e-Binder showcases the full line of products and services needed for your organization's ID needs.
© ColorID, LLC - 2023 | All Rights Reserved