|
Prox card, proxie card, keycard, hid card, smart card, access badge, corporate 1000 card, 26 bit card – whatever you call it, the 125 kHz radio frequency card is still the most widely used card for electronic access in North America. Unfortunately, few people are aware of recent developments that threaten the security status of these familiar cards.
The word “prox” is an abbreviation of “proximity,” which just means “near.” Proximity cards are a significant upgrade for users of mag stripe or Wiegand access cards, which have to be swiped through a reader. Prox cards only need to be held near a reader to open a door, and they work through a wallet, purse, pants pocket or whatever else they are in at the time. Cardholders have enjoyed the convenience of prox cards for nearly three decades. |
|
Choosing the right PACS Reader for your organization
|
When an organization considers migrating to a contactless smart credential, an important part of the process is picking readers for the new credential. Sometimes the reader decision has first priority and dictates the type of credential. In either case, here is the latest on readers for access control.
Existing Readers Installed readers across your facility are typically not uniform. Most organizations have been installing new readers as an ongoing process in new and remodel construction, and replacing old readers when they fail. Regardless of the credential type being used, the newly installed readers are usually off-the-shelf multitech models, meaning they can read low frequency prox credentials and some standard contactless smart credentials. If mag stripe credentials are still in use, the readers may also include that technology. These readers do offer a migration path to newer, more secure credentials for schools that have gone through that process already, but if the reader specification is not examined the organization may find its future credential type choices limited. |
by: David Stallsmith
Director of Product Management |
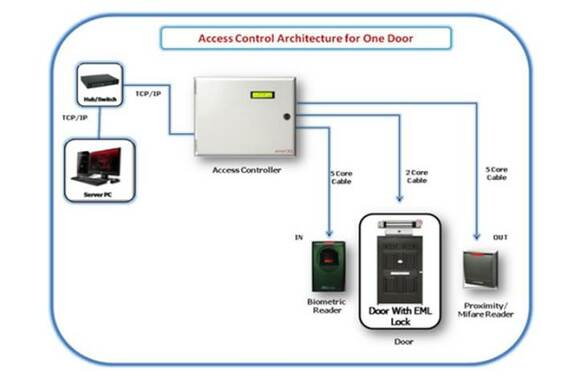
Reader-to-System Communication
Most access control readers communicate with the system, usually a hardware control panel, over Wiegand wiring. This protocol sends 0s and 1s over two wires, in the clear. The simplicity has enabled interoperability for most readers and panels, but the convenience has been superseded by security vulnerabilities as new, inexpensive technology tools have appeared that can read and inject credential data over the unencrypted protocol without detection.
OSDP (Open Supervised Device Protocol), IP and WiFi are newer protocols available in many readers, that support encrypted data transmission and bi-directional communication with control panels or servers, but they each require specific support by the panels themselves.
Migrating to a more secure infrastructure can be approached as a multiyear process, starting with readers that initially communicate over Wiegand, then flashing them to use a more secure, bi-directional protocol when servers, panels, and cabling, if necessary, are upgraded. Readers that support the anticipated protocol can be ordered with that additional feature and begin to be installed immediately.
Brands
Newer reader models can support a variety of methods for using a mobile device to open doors. BLE (Bluetooth Low Energy) and NFC (Near Field Communication) allow readers to communicate with mobile devices in a similar manner to credentials, so readers thus configured can replace existing readers without infrastructure change. Geolocation and mobile apps for user input require communication between the mobile devices and server, over WiFi or cell, so they require specific system support. These latter methods may not require readers at all, since the system could send an “open” or “close” signal directly to an electronically operated lock or door strike.
Most access control readers communicate with the system, usually a hardware control panel, over Wiegand wiring. This protocol sends 0s and 1s over two wires, in the clear. The simplicity has enabled interoperability for most readers and panels, but the convenience has been superseded by security vulnerabilities as new, inexpensive technology tools have appeared that can read and inject credential data over the unencrypted protocol without detection.
OSDP (Open Supervised Device Protocol), IP and WiFi are newer protocols available in many readers, that support encrypted data transmission and bi-directional communication with control panels or servers, but they each require specific support by the panels themselves.
Migrating to a more secure infrastructure can be approached as a multiyear process, starting with readers that initially communicate over Wiegand, then flashing them to use a more secure, bi-directional protocol when servers, panels, and cabling, if necessary, are upgraded. Readers that support the anticipated protocol can be ordered with that additional feature and begin to be installed immediately.
Brands
Newer reader models can support a variety of methods for using a mobile device to open doors. BLE (Bluetooth Low Energy) and NFC (Near Field Communication) allow readers to communicate with mobile devices in a similar manner to credentials, so readers thus configured can replace existing readers without infrastructure change. Geolocation and mobile apps for user input require communication between the mobile devices and server, over WiFi or cell, so they require specific system support. These latter methods may not require readers at all, since the system could send an “open” or “close” signal directly to an electronically operated lock or door strike.
|
Electronic Locks
Schlage and ASSA ABLOY typically embed the same credential-reading technology in their locks as in their wall-mount readers. However, there can be some variation in the list of credential types supported by each lock model, for both manufacturers. For example, newer Schlage locks may not support all variations of low frequency prox, and not all ASSA locks support HID BLE mobile credentials unless they’ve been upgraded. SALTO locks employ a proprietary application on HID MIFARE and DESFire EV1 credentials, but it may be possible to encode additional credentials for use at other readers on these credentials. Other lock manufacturers that support contactless smart credentials may also allow their credentials to share credential memory with other applications. In any case, be sure to test for compatibility between specific credential encoding you want to read and the lock you are interested in. |
Conclusion
New readers from many manufacturers are able to read credentials from more types of devices, with more encoding profiles than ever. They are also available with many different protocols for communicating with the access control system. Installing thoughtfully configured readers now, rather than generic, multi-purpose models from an installer’s stock, can lead the way for more secure and convenient access control options in the future.
New readers from many manufacturers are able to read credentials from more types of devices, with more encoding profiles than ever. They are also available with many different protocols for communicating with the access control system. Installing thoughtfully configured readers now, rather than generic, multi-purpose models from an installer’s stock, can lead the way for more secure and convenient access control options in the future.
Request additional information or pricing,
please submit the below contact form:
please submit the below contact form:
|
|
|
|
WE'RE HERE TO HELP.
|
ColorID has spent over 24 years serving the ID Industry with top-level sales and support to build the ultimate trust with every customer.
|
|
|
|
ColorID's interactive e-Binder showcases the full line of products and services needed for your organization's ID needs.
© ColorID, LLC - 2023 | All Rights Reserved